Protect Your Information With Trusted Cloud Storage Solutions
By exploring the subtleties of relied on cloud storage services, you can make sure that your data is shielded from susceptabilities and unapproved gain access to. The discussion around guarding your information with these solutions dives right into detailed details that can make a substantial difference in your information security approach.
Significance of Information Protection in Cloud Storage Space
Data safety and security is critical in cloud storage services to safeguard sensitive details from unauthorized gain access to and potential breaches. As even more organizations and people migrate their information to the cloud, the demand for durable protection measures has ended up being increasingly vital. Cloud storage carriers need to implement encryption methods, gain access to controls, and invasion detection systems to guarantee the discretion and stability of saved data.
Among the main obstacles in cloud storage safety is the common duty model, where both the service provider and the user are responsible for safeguarding data. While providers are in charge of safeguarding the infrastructure, individuals must take steps to shield their data via solid passwords, multi-factor verification, and routine safety and security audits. Failing to carry out proper safety measures can reveal data to cyber dangers such as hacking, malware, and information breaches, bring about economic loss and reputational damage.
To address these individuals, threats and services must carefully vet cloud storage space providers and select relied on services that focus on information protection. By partnering with credible companies and adhering to best practices, users can alleviate safety and security threats and with confidence take advantage of the advantages of cloud storage space solutions.
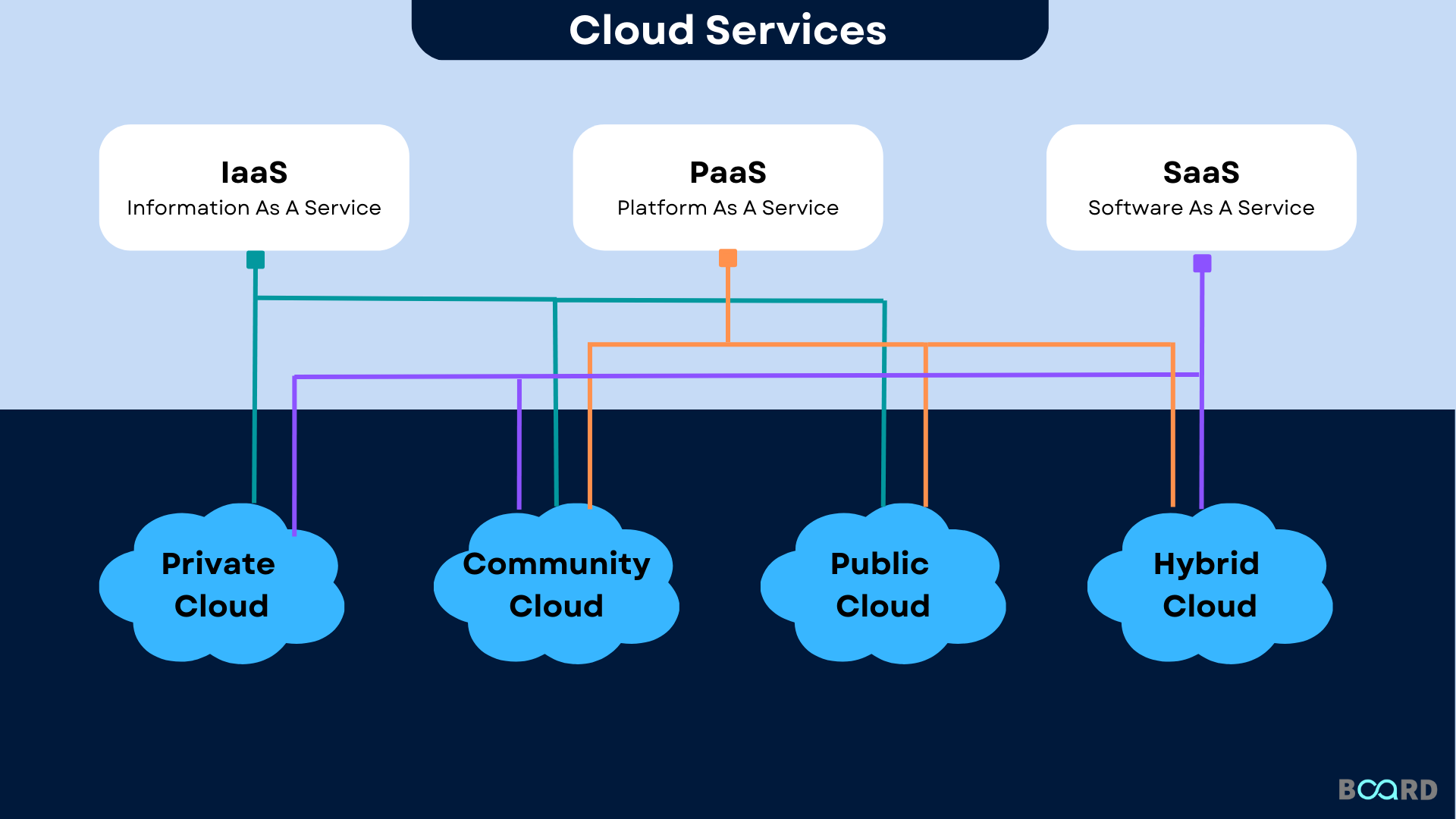
Benefits of Utilizing Trusted Suppliers
Offered the enhancing focus on data safety in cloud storage space solutions, recognizing the benefits of utilizing trusted carriers comes to be critical for protecting sensitive info - cloud services press release. Relied on cloud storage space carriers use a variety of advantages that contribute to ensuring the safety and security and integrity of kept information. By choosing a relied on cloud storage space company, companies and people can profit from enhanced information protection measures and tranquility of mind concerning the safety of their useful details.

Factors to Consider When Picking
When selecting a cloud storage space service supplier, it is important to think about numerous elements to guarantee optimal information security and capability. Research the firm's track record, uptime guarantees, and customer reviews to guarantee they have a background of consistent service and information defense. By carefully advice considering these factors, you can pick a cloud storage space solution provider that fulfills your information protection requires effectively.
Finest Practices for Information Security
To ensure robust data security, applying industry-standard safety methods is vital for guarding delicate info stored in cloud storage space solutions. File encryption plays a critical duty in safeguarding information both en route and at rest (linkdaddy cloud services press release). Using solid encryption formulas makes sure that also if unauthorized accessibility occurs, the information stays unreadable and secured. Additionally, carrying out multi-factor authentication adds an extra layer of protection by needing individuals to give two or more forms of verification before acquiring accessibility to the data. Regularly upgrading software and systems is necessary to spot any susceptabilities that cyberpunks could make use of. Carrying out constant protection audits and analyses helps recognize prospective weaknesses in the data protection steps and permits for timely removal. Developing and applying strong password plans, establishing gain access to controls based on the concept of the very least advantage, and enlightening individuals on cybersecurity best methods are additionally essential parts of an extensive information security approach in cloud storage services.
Ensuring Data Personal Privacy and Conformity
Relocating ahead from the emphasis on data security procedures, a vital element that companies need to address in cloud storage space solutions is making sure information privacy and compliance with pertinent regulations and criteria. Organizations need to implement file encryption, gain access to controls, and normal protection audits to protect data personal privacy in cloud storage.
To make sure information personal privacy and conformity, companies ought to choose cloud storage suppliers that provide robust protection measures, clear data taking care of plans, and compliance certifications. Carrying out due persistance on the carrier's protection methods, information file investigate this site encryption methods, and information residency policies is important.
Final Thought
In final thought, prioritizing data safety and security with reliable cloud storage solutions is important for safeguarding delicate info from cyber threats. Eventually, shielding your data with relied on carriers assists reduce risks and keep information privacy and compliance (Cloud Services).
The discussion around safeguarding your information with these services digs into intricate information that can make a significant difference in your data safety and security approach.
Moving forward from the emphasis on data security measures, an essential facet that companies should address in cloud storage services is making certain data personal privacy and content conformity with pertinent regulations and criteria.To guarantee data privacy and compliance, organizations need to select cloud storage carriers that supply robust protection actions, clear data managing plans, and compliance certifications. Performing due persistance on the provider's security techniques, data security techniques, and data residency policies is crucial. Furthermore, organizations ought to develop clear data administration plans, perform normal conformity analyses, and give team training on data personal privacy and safety and security procedures.